token-based card access control system Token-based authentication is a passwordless security mechanism that validates a user's identity through the use of tokens. A token is a unique piece of data, often a string of characters, that . Link 1: what phones are compatible?https://www.nfcw.com/nfc-phones-list/Link 2: Tagmo App Downloadhttps://drive.google.com/file/d/1dL4wSEx3cnJJSL2hfNyI_MLvHD.A Magic card is a card that allows you to change its UID. Generally, NFC cards have a UID pre .
0 · what is token based authentication
1 · token based authentication entrust
2 · token based authentication control
3 · token based authentication api
4 · token based access control
5 · okta token based authentication
6 · identity provider token based authentication
7 · how to get token based authentication
Tesla Key Ring enables lock, unlock and start of Tesla model 3, model Y, model X 2021+ and Model S 2021+ Skip to content. 🚚 Free worldwide delivery🌎 How It Works? FAQ About us Order Status . Gift Card. From $99.00. Jeans. $139.00. No Charging
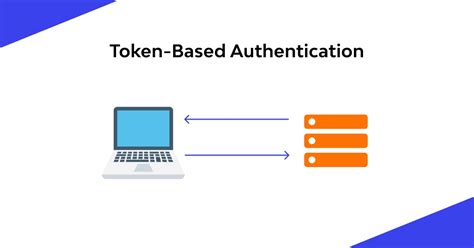
Token-based authentication is different from traditional password-based or server-based authentication techniques. Tokens offer a second layer of security, and administrators have detailed control over each action and transaction. But using tokens requires a bit of coding .
Token-based authentication is a passwordless security mechanism that validates a user's identity through the use of tokens. A token is a unique piece of data, often a string of characters, that .Second, this paper proposes a solution by giving the general data structure of access control token, elaborating the equivalence, split, merge and verification algorithms of access control .
Token-based authentication is an authentication protocol where users verify their identity in exchange for a unique access token. Users can then access the website, application, or .
Token-based authentication is different from traditional password-based or server-based authentication techniques. Tokens offer a second layer of security, and administrators have detailed control over each action and transaction. But .Token-based authentication is a passwordless security mechanism that validates a user's identity through the use of tokens. A token is a unique piece of data, often a string of characters, that acts as a stand-in for the user's credentials.Second, this paper proposes a solution by giving the general data structure of access control token, elaborating the equivalence, split, merge and verification algorithms of access control token, and explaining the system architecture of token-based access control.Token-based authentication is an authentication protocol where users verify their identity in exchange for a unique access token. Users can then access the website, application, or resource for the life of the token without having to re-enter their credentials.
The microservice access control method is based on a token strategy that increases security in access control by distinguishing between authentication and authorization services, the issued tokens of which are trusted by the resource microservices.Token-based authentication is the process of verifying identity by checking a token. In access management, servers use token authentication to check the identity of a user, an API, a computer, or another server.
Access control is one of the most basic and essential security measures used in data centers. It is underpinned by effective user authentication measures. Choosing the right combination of access control and authentication measures is key to effective data center security. Here is a quick guide to what you need to know.
what is token based authentication
token based authentication entrust
how to copy nfc tag android
Second, this paper proposes a solution by giving the general data structure of access control token, elaborating the equivalence, split, merge and verification algorithms of access control. Token-Based Access Control is a security technique where a validated user is given a digital token, enabling them to access a system or network. Social media platforms, online banking, and cloud services like Google Drive and Dropbox frequently use this . Token-based access control (TBAC) enhances the manageability of authorization through the token. However, traditional access control policies lack the ability to dynamically adjust based on user access behavior. Incorporating user reputation evaluation into access control can provide valuable feedback to enhance system security and flexibility.
Token-based authentication is different from traditional password-based or server-based authentication techniques. Tokens offer a second layer of security, and administrators have detailed control over each action and transaction. But .Token-based authentication is a passwordless security mechanism that validates a user's identity through the use of tokens. A token is a unique piece of data, often a string of characters, that acts as a stand-in for the user's credentials.Second, this paper proposes a solution by giving the general data structure of access control token, elaborating the equivalence, split, merge and verification algorithms of access control token, and explaining the system architecture of token-based access control.
Token-based authentication is an authentication protocol where users verify their identity in exchange for a unique access token. Users can then access the website, application, or resource for the life of the token without having to re-enter their credentials. The microservice access control method is based on a token strategy that increases security in access control by distinguishing between authentication and authorization services, the issued tokens of which are trusted by the resource microservices.
Token-based authentication is the process of verifying identity by checking a token. In access management, servers use token authentication to check the identity of a user, an API, a computer, or another server.
Access control is one of the most basic and essential security measures used in data centers. It is underpinned by effective user authentication measures. Choosing the right combination of access control and authentication measures is key to effective data center security. Here is a quick guide to what you need to know. Second, this paper proposes a solution by giving the general data structure of access control token, elaborating the equivalence, split, merge and verification algorithms of access control. Token-Based Access Control is a security technique where a validated user is given a digital token, enabling them to access a system or network. Social media platforms, online banking, and cloud services like Google Drive and Dropbox frequently use this .
copy a nfc tag
token based authentication control
In 2018, Xiaomi’s Mi6X and Mi8 contained an NFC chip, and had Android Pay and Beam functionality. In 2020, the Mi10 and Mi10T and their following models also came equipped with NFC. All of Xioami’s “Mi Mix” .Method 2: Looking for signs on the card: Some cards may have visible indications indicating the presence of RFID or NFC technology. Look for any logos or symbols on the card that suggest contactless communication. Common symbols include the “waves” symbol for .
token-based card access control system|token based access control