smart card based security access control system project The installation of access control typically includes the following steps: Run cabling and wiring for hardware. Install control panels, keypads, readers, locks, and cameras as needed. Configure the system to match facility requirements. Integrate with existing security equipment if necessary. Inspect and test the system for proper function. The largest Selection of Digital Business Cards, Tags & More. All Tap Tags have Tap NFC Technology to seamlessly share a digital profile or review page with any smartphone. A free dashboard is included with all products to edit or manage your profile from any computer. Most Tap Tags can be customized with your own artwork, all with an industry .
0 · Integrating Access Control Systems Into Existing
1 · Efficient and secure access control system based on
The Philadelphia Eagles easily beat the Tampa Bay Buccaneers, 21 to 3, in the 2000 NFC Wild Card game on December 31, 2000. Sun, Dec 31, 2000. Buccaneers. 3. Eagles. 21. Final. Sat, .
In this paper, we present our smart-card-based access control system based on modern .
quickbooks contactless chip and magstripe card reader
The installation of access control typically includes the following steps: Run cabling and wiring for hardware. Install control panels, keypads, readers, locks, and cameras as needed. Configure the system to match facility requirements. .In this paper, we present our smart-card-based access control system based on modern programmable smart cards. We propose an efficient and secure authentication protocol that is based on a zero-knowledge authentication method.The installation of access control typically includes the following steps: Run cabling and wiring for hardware. Install control panels, keypads, readers, locks, and cameras as needed. Configure the system to match facility requirements. Integrate with existing security equipment if necessary. Inspect and test the system for proper function.
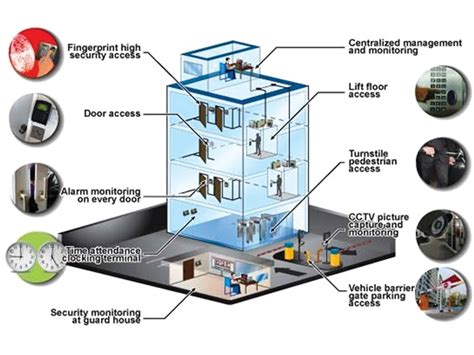
This paper discusses and proposes the design of a centralized smart card-based security and surveillance system for a prototype property with the use of cost effective components and.This research comprehensively integrates all the functionalities of the smart card to get one base application which a web service which can provide access to may functionalities of the smart card based on it usage.Card access systems are a type of access control system used primarily in commercial properties to enhance security and manage access to specific areas. These systems are designed to grant or restrict entry, ensuring that only authorized individuals can access sensitive locations within a facility. The primary purpose of these systems is to .
In this paper, two-level authentications based on smart card and pin code access control is presented. This system was developed and implemented for a small size sliding door. The sliding operation was carried out by motor controlled pinion and rack. The system at all times provided access or limitation accordingly.
In this paper, two-level authentications based on smart card and pin code access control is presented. This system was developed and implemented for a small size sliding door.
Smart cards are most often used in applications which strictly require security and substantiation. Connect people and spaces. Learn all about smart card access control systems in our detailed guide and find out what type of smart card door access systems are best for you.
Most of us have had to present identification to enter a building, a room within a building, a garage, a gate, a secured perimeter, or even a highway. Typically, forms of identification used in such physical access scenarios include badges, RFID tags, smart cards, or other tokens. In this paper, a prototyped door security system is designed to allow a privileged user to access a secure keyless door where valid smart card authentication guarantees an entry.In this paper, we present our smart-card-based access control system based on modern programmable smart cards. We propose an efficient and secure authentication protocol that is based on a zero-knowledge authentication method.
The installation of access control typically includes the following steps: Run cabling and wiring for hardware. Install control panels, keypads, readers, locks, and cameras as needed. Configure the system to match facility requirements. Integrate with existing security equipment if necessary. Inspect and test the system for proper function. This paper discusses and proposes the design of a centralized smart card-based security and surveillance system for a prototype property with the use of cost effective components and.
This research comprehensively integrates all the functionalities of the smart card to get one base application which a web service which can provide access to may functionalities of the smart card based on it usage.Card access systems are a type of access control system used primarily in commercial properties to enhance security and manage access to specific areas. These systems are designed to grant or restrict entry, ensuring that only authorized individuals can access sensitive locations within a facility. The primary purpose of these systems is to .In this paper, two-level authentications based on smart card and pin code access control is presented. This system was developed and implemented for a small size sliding door. The sliding operation was carried out by motor controlled pinion and rack. The system at all times provided access or limitation accordingly. In this paper, two-level authentications based on smart card and pin code access control is presented. This system was developed and implemented for a small size sliding door.
Smart cards are most often used in applications which strictly require security and substantiation. Connect people and spaces. Learn all about smart card access control systems in our detailed guide and find out what type of smart card door access systems are best for you.
Most of us have had to present identification to enter a building, a room within a building, a garage, a gate, a secured perimeter, or even a highway. Typically, forms of identification used in such physical access scenarios include badges, RFID tags, smart cards, or other tokens.
Integrating Access Control Systems Into Existing
Efficient and secure access control system based on
At Evrycard, we strive to provide quick and efficient service. Here’s a breakdown of the typical timeline for orders within the UK: Design Process: It generally takes 1 working day to complete the design process of the NFC business card, .
smart card based security access control system project|Efficient and secure access control system based on