security bit of tag rfid modification illegal Radio Frequency Identification (RFID) tags require a radio signal emitted by the receiver in order to read them. Due to this, they operate within a limited distance and are not capable of transmitting large amounts of data. Examples of RFID tags can be seen in credit cards and door passes. Active Tags. Auburn Sports & Live Shows. Auburn Football. Auburn Basketball. Premium Stations. Auburn Football. Powered by Playfly Sports. Listen to Stream Auburn Tigers Sports Network here on .
0 · why is rfid safe
1 · what is rfid technology
2 · rfid systems
3 · rfid security vulnerability
4 · rfid security risks
5 · rfid encryption
6 · rfid card copy and paste
7 · benefits of rfid technology
Fans can listen to free, live streaming audio of Auburn Sports Network radio broadcasts of Tiger games and coach's shows. Listen on. Computer; Radio
If a transit company is issuing transponders with unique serial numbers and allowing people to ride its busses as long as the ID in a transponder appears valid, then a criminal could buy an RFID card on the Internet, write the ID of a legitimate card to the transponder with an RFID . Radio Frequency Identification (RFID) tags require a radio signal emitted by the receiver in order to read them. Due to this, they operate within a limited distance and are not capable of transmitting large amounts of data. Examples of RFID tags can be seen in credit cards and door passes. Active Tags.Besides being vulnerable to common attacks such as eavesdropping, man-in-the-middle, and denial of service, RFID technology is, in particular, susceptible to spoofing and power attacks . Examples include attacks employing unauthorized tag reading, modification of tag data, and attacks in the application middleware. Strategic layer includes all attacks that target .
Like any other security devices and mechanism RFID is not flawless. Despite its widespread application and usage, RFID poses security threats and challenges that need to be addressed . 7. There are RFID tags which can be cloned.
RFID attacks are currently conceived as properly formatted but fake RFID data; however no one expects an RFID tag to send a SQL injection attack or a buffer overflow.Security attacks on RFID may target the physical tag, the communication channel between the tag and the reader, or the applications system. Table 1 allows us to classify the existing security .
why is rfid safe

1. In the UK, what does the law say regarding the legality of cloning RFID tags that you own, but did not generate? I'm particularly interested in cases like the Mifare Classic tags, where you may need to perform an exploit to find encryption keys in order to clone the tag. united-kingdom. encryption. security. Share. Improve this question. Radio Frequency Identification (RFID) tags require a radio signal emitted by the receiver in order to read them. Due to this, they operate within a limited distance and are not capable of transmitting large amounts of data. Examples of RFID tags can be seen in credit cards and door passes. Active Tags.Besides being vulnerable to common attacks such as eavesdropping, man-in-the-middle, and denial of service, RFID technology is, in particular, susceptible to spoofing and power attacks (Figure 2). This section illustrates different kinds of attacks and provides countermeasures against these attacks. Fig. 2.
Examples include attacks employing unauthorized tag reading, modification of tag data, and attacks in the application middleware. Strategic layer includes all attacks that target the business processes and objectives of organizations that use RFID systems.
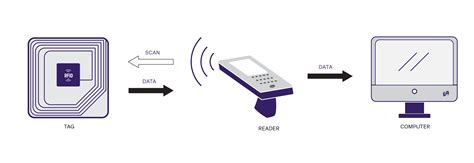
Security issues in RFID system. The RFID scheme consists of several classes of tags and reader. These tags include an inadequate amount of memory and low-power capacity. However, there are numerous other issues in terms of .Attackers can write information to a basic black tag or can modify data in the tag writable basic tag in order to gain access or validate a product’s authenticity. The things that an attacker can do with basic tags are: RFID tags can be cloned. Tags which do not make use of password-protection or over-the-air (OTA) encryption can have their data banks copied into new tags. RFID tags (at least Class 1 Generation 2 tags, aka UHF RFID tags) are computationally active, not passive. 1. In the UK, what does the law say regarding the legality of cloning RFID tags that you own, but did not generate? I'm particularly interested in cases like the Mifare Classic tags, where you may need to perform an exploit to find encryption keys in order to clone the tag. united-kingdom. encryption. security. Share. Improve this question.
RFID tags are vulnerable to DoS/Desynchronization attacks because RFID tag and reader send out radio signals to each other in the open. Barcodes only reflect the beam of light received from the reader. RFID attacks are currently conceived as properly formatted but fake RFID data; however no one expects an RFID tag to send a SQL injection attack or a buffer overflow. The cloning attack using clone tags to impersonate genuine tags can lead to unimaginable threats because RFID applications equate tag genuineness to the authenticity of tagged objects. Proposed countermeasures, however, keep showing limitations in effectiveness, efficiency, security, privacy, or applicability as new RFID applications emerge.
Radio Frequency Identification (RFID) tags require a radio signal emitted by the receiver in order to read them. Due to this, they operate within a limited distance and are not capable of transmitting large amounts of data. Examples of RFID tags can be seen in credit cards and door passes. Active Tags.Besides being vulnerable to common attacks such as eavesdropping, man-in-the-middle, and denial of service, RFID technology is, in particular, susceptible to spoofing and power attacks (Figure 2). This section illustrates different kinds of attacks and provides countermeasures against these attacks. Fig. 2. Examples include attacks employing unauthorized tag reading, modification of tag data, and attacks in the application middleware. Strategic layer includes all attacks that target the business processes and objectives of organizations that use RFID systems.
Security issues in RFID system. The RFID scheme consists of several classes of tags and reader. These tags include an inadequate amount of memory and low-power capacity. However, there are numerous other issues in terms of .
Attackers can write information to a basic black tag or can modify data in the tag writable basic tag in order to gain access or validate a product’s authenticity. The things that an attacker can do with basic tags are:
RFID tags can be cloned. Tags which do not make use of password-protection or over-the-air (OTA) encryption can have their data banks copied into new tags. RFID tags (at least Class 1 Generation 2 tags, aka UHF RFID tags) are computationally active, not passive. 1. In the UK, what does the law say regarding the legality of cloning RFID tags that you own, but did not generate? I'm particularly interested in cases like the Mifare Classic tags, where you may need to perform an exploit to find encryption keys in order to clone the tag. united-kingdom. encryption. security. Share. Improve this question. RFID tags are vulnerable to DoS/Desynchronization attacks because RFID tag and reader send out radio signals to each other in the open. Barcodes only reflect the beam of light received from the reader.
RFID attacks are currently conceived as properly formatted but fake RFID data; however no one expects an RFID tag to send a SQL injection attack or a buffer overflow.
what is rfid technology
identive cloud 2700 r smart card reader driver
rfid systems
Mix 96.7. Auburn and Opelika's Christmas Station Delana. Entertainment News. Timothèe Chalamet Told To Change His Look Before Auditioning For Big Movies Nov 12, 2024. Listen To Us Anytime On The Free iHeartRadio App. iHeart: All .A list of AM and FM radio stations near the city of Auburn, Alabama. Callsign: Zip code: City: State: Toggle navigation. Radio News; Radio Markets . Auburn, Alabama Radio .
security bit of tag rfid modification illegal|why is rfid safe