smart card based user authentication protocol In a recent paper, Das proposed a smart card‒based anonymous user . No, because he’s a new villager for this game and the amiibo cards were launched before he existed. Maybe they’ll come out with a new pack though. 13. Reply. Differentiated-Imp. • 4 yr. .The simplest (and most common) use case for this library is to read NFC tags containing NDEF, which can be achieved via the following codes: import React from 'react'; import {View, Text, TouchableOpacity, StyleSheet} from 'react .
0 · what is smart card authentication
1 · smart card two factor authentication
2 · smart card certificate authentication
3 · smart card based identification system
4 · smart card authentication step by
5 · smart card authentication process
6 · configure smart card authentication
7 · authenticate using your smart card
When you scan your warranty card into your web browser it will open up the Rolex main web page only. It will not open up to your exact model. Not sure what data Rolex stores on the chip within the the warranty card.
We adapt a pair of dynamic IDs to realize the user's anonymity, and present a novel nonce-based authentication approach. Our protocol eliminates all identified security flaws in original protocols. Furthermore, high performance and other good functionalities are preserved.To address these concerns, we propose a lightweight privacy-preserving .
Development of a novel security protocol based on smart cards for IoT networks. . Smart-card-based authentication is one of the most convenient and commonly . In a recent paper, Das proposed a smart card‒based anonymous user .
In this paper, we proposed an efficient robust smart card and remote client . Our purpose for this paper is to propose a smart card-based protocol that .
In this section, we briefly review Hsiang–Shih's remote authentication protocol ( .
We adapt a pair of dynamic IDs to realize the user's anonymity, and present a novel nonce-based authentication approach. Our protocol eliminates all identified security flaws in original protocols. Furthermore, high performance and other good functionalities are preserved. Development of a novel security protocol based on smart cards for IoT networks. ScPUAK is based on Elliptic curve cryptography, user’s biometry and hash functions. The formal security analysis shows its efficiency and safety against known attacks. Smart-card-based authentication is one of the most convenient and commonly used authentication mechanisms, as remarked in Ref. 1. It only requires a client to remember a memorable password and to hold a personal smart card, where the smart card stores a secret key and is issued by the server.
In a recent paper, Das proposed a smart card‒based anonymous user authentication protocol for wireless communications. The scheme can protect user privacy and is believed to be secure against a range of network attacks even if the secret information stored in the smart card is compromised.
In this paper, we proposed an efficient robust smart card and remote client password-based authentication protocol based on extended chaotic maps under smart city environment using IoT, where the client can get relieve from different attacks. Our purpose for this paper is to propose a smart card-based protocol that enables mutual authentication between a user and a server and allows for the establishment of a secure session key. In this context, we use Elliptic curve cryptography (ECC) and other lightweight operations as hash function and exclusive OR (XOR). In this section, we briefly review Hsiang–Shih's remote authentication protocol ( Hsiang and Shih, 2009) which consists of four phases, i.e. registration phase, login phase, verification phase and password change phase. To address these concerns, we propose a lightweight privacy-preserving authentication protocol in which the physically unclonable function is considered a necessary tool. The suggested technique avoids creating a significant number of .
For many industrial applications, the smart card is a necessary safety component in user authentication. Smart cards provided to the users are used in open and public places, making them susceptible to physical and cloning attacks. Thus, the opponent can break the authentication process without the smart card if the information is exposed.
Security Protocols. Article. ScPUAK: Smart card-based secure Protocol for remote User Authentication and Key agreement. August 2023. Computers & Electrical Engineering 109.We adapt a pair of dynamic IDs to realize the user's anonymity, and present a novel nonce-based authentication approach. Our protocol eliminates all identified security flaws in original protocols. Furthermore, high performance and other good functionalities are preserved. Development of a novel security protocol based on smart cards for IoT networks. ScPUAK is based on Elliptic curve cryptography, user’s biometry and hash functions. The formal security analysis shows its efficiency and safety against known attacks.
Smart-card-based authentication is one of the most convenient and commonly used authentication mechanisms, as remarked in Ref. 1. It only requires a client to remember a memorable password and to hold a personal smart card, where the smart card stores a secret key and is issued by the server.
In a recent paper, Das proposed a smart card‒based anonymous user authentication protocol for wireless communications. The scheme can protect user privacy and is believed to be secure against a range of network attacks even if the secret information stored in the smart card is compromised.
In this paper, we proposed an efficient robust smart card and remote client password-based authentication protocol based on extended chaotic maps under smart city environment using IoT, where the client can get relieve from different attacks. Our purpose for this paper is to propose a smart card-based protocol that enables mutual authentication between a user and a server and allows for the establishment of a secure session key. In this context, we use Elliptic curve cryptography (ECC) and other lightweight operations as hash function and exclusive OR (XOR). In this section, we briefly review Hsiang–Shih's remote authentication protocol ( Hsiang and Shih, 2009) which consists of four phases, i.e. registration phase, login phase, verification phase and password change phase.
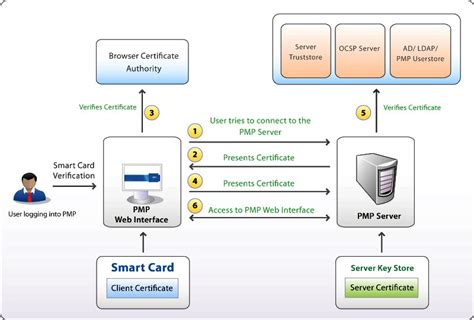
To address these concerns, we propose a lightweight privacy-preserving authentication protocol in which the physically unclonable function is considered a necessary tool. The suggested technique avoids creating a significant number of .For many industrial applications, the smart card is a necessary safety component in user authentication. Smart cards provided to the users are used in open and public places, making them susceptible to physical and cloning attacks. Thus, the opponent can break the authentication process without the smart card if the information is exposed.
what is smart card authentication

smart and final gift cards online
scr35xx smart card reader
2. Use the keys to read all data blocks of that card 3. Clone i.e. write the data blocks into a .
smart card based user authentication protocol|what is smart card authentication