smart card based authentication mechanisms Using a smart card in conjunction with a password can add an extra layer of security to protect sensitive patient or customer data. An additional layer of security can be . nfc-cardreader-example-written-in-php.php This file contains bidirectional Unicode text that .
0 · what is smart card authentication
1 · smart card two factor authentication
2 · smart card certificate authentication
3 · smart card based identification system
4 · smart card authentication step by
5 · smart card authentication process
6 · configure smart card authentication
7 · authenticate using your smart card
It is possible physically for the phone hardware but there are software problems, payment works but it's provided by google. I read about using phone as nfc tag recently and .
Digital authentication against data stored on a smartcard: Smartcards are capable authenticating a person offline with a higher level of assurance.
Digital authentication against data stored on a smartcard: Smartcards are capable authenticating a person offline with a higher level of assurance.Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that .
Using a smart card in conjunction with a password can add an extra layer of security to protect sensitive patient or customer data. An additional layer of security can be . Smart card authentication is a two-step login process that uses a smart card. The smart card stores a user’s public key credentials and a personal identification number (PIN), .
Authentication. This inspects, then confirms, the proper identity of people involved in a transaction of data or value. In authentication systems, authentication is measured by assessing the .Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or . Smart-card-based authentication is one of the most convenient and commonly used authentication mechanisms, as remarked in Ref. 1. It only requires a client to remember . As the most prevailing two-factor authentication mechanism, smart-card-based password authentication has been a subject of intensive research in the past two decades, .
In this paper, we aim to propose a new robust and effective password-based remote user authentication scheme using smart card. Our scheme is efficient, because our scheme uses .
Smart-card based password authentication has been the most widely used two-factor authentication (2FA) mechanism for security-critical applications (e.g., e-Health, smart .Digital authentication against data stored on a smartcard: Smartcards are capable authenticating a person offline with a higher level of assurance.Storing the cryptographic keys in a secure central location makes the authentication process scalable and maintainable. For smart cards, Windows supports a provider architecture that .
Using a smart card in conjunction with a password can add an extra layer of security to protect sensitive patient or customer data. An additional layer of security can be .
Smart card authentication is a two-step login process that uses a smart card. The smart card stores a user’s public key credentials and a personal identification number (PIN), .Authentication. This inspects, then confirms, the proper identity of people involved in a transaction of data or value. In authentication systems, authentication is measured by assessing the .Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or . Smart-card-based authentication is one of the most convenient and commonly used authentication mechanisms, as remarked in Ref. 1. It only requires a client to remember .
As the most prevailing two-factor authentication mechanism, smart-card-based password authentication has been a subject of intensive research in the past two decades, .In this paper, we aim to propose a new robust and effective password-based remote user authentication scheme using smart card. Our scheme is efficient, because our scheme uses .
rfid tracking in manufacturing
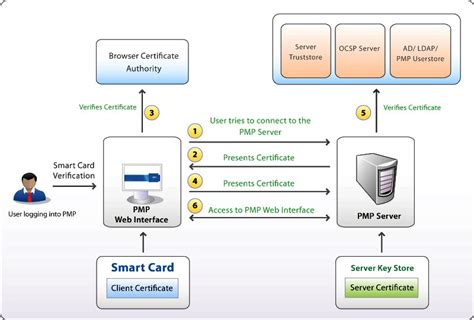
what is smart card authentication

An NFC tag is a small integrated circuit consisting of a copper coil and some amount of storage. Data can be read or written to this tag only when another NFC device is brought near it because it .
smart card based authentication mechanisms|smart card authentication process